views
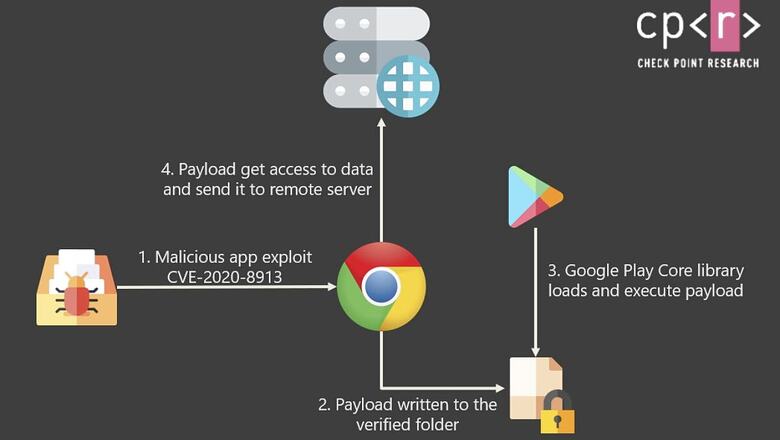
A number of popular apps, including dating apps OKCupid and Grindr, travel app Bumble, e-commerce app Indiamart and Microsoft apps Edge and Teams on the Google Play Store, have been found to have sported a key vulnerability that could have allowed hackers to have stolen your banking data, and even bypassed two-factor authentication on your phone. Revealed in its security research blog on December 3, by Check Point researchers Aviran Hazum and Jonathan Shimonovich, the report reveals the flaw as a known vulnerability, registered as CVE-2020-8913. It affects the Google Play Core Library, which is used by a large number of rather popular apps such as Google Chrome, Facebook, Instagram and so on. What’s alarming to note is that Google had already issued a patch for the vulnerability way back in April 2020. However, despite Google’s initial security patch, the flaws seemingly remained, and in the interim period, affected a large number of rather popular apps on the Google Play Store.
The source of the flaw was the Google Play Core runtime library, which controlled an app’s interaction with the Google Play Store servers for a wide number of reasons. These reasons could be downloading of additional resources required by an app, pushing updates an in-app updates, and registering in-app reviews. The vulnerability in question lay in the architecture of how the Google Play Core Library communicates with an app — while Google typically uses a safe, sandboxed or isolated area of the app in question to relay verified updates, there is also a separate isolated area within the app’s code framework where third party services relay information to it. With this vulnerability, attackers could tap into the official code sandbox, and use it to inject malicious code into the framework of a legitimate, popular app.
As Check Point reports, this ability to inject infected code into a legitimate app could allow hackers to add malware to any smartphone. This could have then been used to hijack banking credentials, read SMS messages to infiltrate two-factor authentication, break encrypted corporate messaging and file storage apps to access sensitive documents, track smartphone location and social media apps, and even send messages on behalf of the phone’s owner, therefore carrying out a potential end-to-end inflitration of a user.
While Check Point underlines that this rather critical vulnerability has been steadily getting standalone security patches from each of the apps that were exposed to the flaw, it is not quite clear as to how many more such apps still remain vulnerable to this. As the best possible precautionary measure, users are always urged to update their apps at the soonest, not download any more apps than what’s necessary, and if possible, isolate all banking, financial and work related sensitive tasks to a separate smartphone.
Read all the Latest News, Breaking News and Coronavirus News here



















Comments
0 comment